Last week I saw an update from one of the Clumio founders on twitter. It reminded me that I had promised to take a look at their product. This week I had a meeting set up with Clumio and we went over their product and how to configure it briefly. Clumio is a SaaS based backup solution that was founded in 2017 by former PernixData, Nutanix, EMC folks. The three founders are Poojan Kumar, Kaustubh Patil, and Woon Jung, and those three you may remember from PernixData. One thing to point out is that they had 3 rounds of funding (~190 million dollars) so far and they came out of stealth around VMworld 2019. Coincidentally they won the Gold award for Best of VMworld in the data protection category, and best of show for the entire show, not bad for a first VMworld. I guess that I have to point out that although I would classify them as backup/recovery today, they are adding new functionality weekly and “backup/recovery” is probably not a fair category, data protection is more appropriate and it would not surprise me if that evolves to data management and protection over time. If you are not a fan of reading, simply head over to my youtube video on Clumio, otherwise, just continue below.
Last week I saw an update from one of the Clumio founders on twitter. It reminded me that I had promised to take a look at their product. This week I had a meeting set up with Clumio and we went over their product and how to configure it briefly. Clumio is a SaaS based backup solution that was founded in 2017 by former PernixData, Nutanix, EMC folks. The three founders are Poojan Kumar, Kaustubh Patil, and Woon Jung, and those three you may remember from PernixData. One thing to point out is that they had 3 rounds of funding (~190 million dollars) so far and they came out of stealth around VMworld 2019. Coincidentally they won the Gold award for Best of VMworld in the data protection category, and best of show for the entire show, not bad for a first VMworld. I guess that I have to point out that although I would classify them as backup/recovery today, they are adding new functionality weekly and “backup/recovery” is probably not a fair category, data protection is more appropriate and it would not surprise me if that evolves to data management and protection over time. If you are not a fan of reading, simply head over to my youtube video on Clumio, otherwise, just continue below.
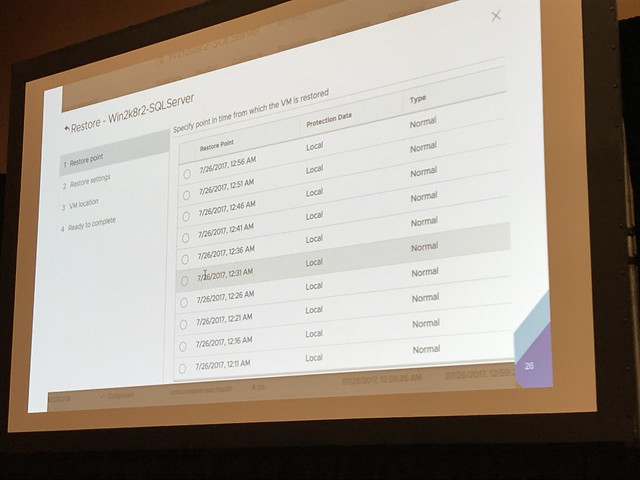
So how does it work conceptually? Well they basically have a SaaS solution, but you will need to install an OVA (they call it a cloud connector) in your environment to connect to the SaaS platform for VMware on-premises and VMware Cloud on AWS. When you connect AWS EBS they use a cloud formation template. This cloud connector is a 4 vCPU/8GB virtual machine that then needs the ability to connect to “the outside world” of course. The Cloud Connector is stateless and requires no updates. You can run this Cloud Connector appliance in multiple clusters, on-prem, or in VMware Cloud on AWS and once they are registered you will see those data sources in your portal. This is nice as you can see all your data sources across public and private clouds in one single pane of glass. You will have the ability to define “backup schemes” by creating policies. These policies can of course then be associated with objects. These objects can be VMs, Clusters and even vCenter Server instances. This means that if you assign a policy to vCenter Server that every new VM created will inherit the policy automatically. You may wonder, where is your data stored? Your data is stored in S3 buckets that are part of the Clumio SaaS-based platform. Customers are isolated from each other, they will have their own dedicated S3 buckets, and these buckets are created and maintained by Clumio, you as a customer only interact with Clumio! [Read more…] about Startup intro: SaaS-based backup solution Clumio

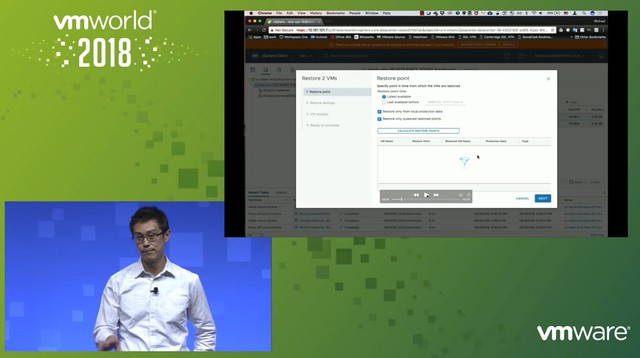 Michael started out with an explanation about what an SSDC brings to customers, and how a digital foundation is crucial for any organization that wants to be competitive in the market. vSAN, of course, is a big part of the digital foundation, and for almost every customer data protection and data recovery is crucial. Michael went over the various vSAN use cases and also the availability and recoverability mechanisms before introducing Native vSAN Data Protection.
Michael started out with an explanation about what an SSDC brings to customers, and how a digital foundation is crucial for any organization that wants to be competitive in the market. vSAN, of course, is a big part of the digital foundation, and for almost every customer data protection and data recovery is crucial. Michael went over the various vSAN use cases and also the availability and recoverability mechanisms before introducing Native vSAN Data Protection.