In Part 1 of this series we described the different layers of networking. We already briefly spoke about Network Pools and that both a vApp Networks and Org Networks consume a segment out of a pool. In order to fully understand vCD (VMware vCloud Director) networking we will need to explain the foundation for all Cloud Internal traffic first which is the Network Pool.
Network Pools
As described in one of my earlier articles vCD mainly revolves around pooling of resources. This also goes for networking and more specifically for the Org Network and the vApp Network. Each vApp and Org Network will consume a network (segment) out of a defined pool. This network pool typically isolates network “segments” on layer 2 from the other networks in the pool. There are currently 3 types of network pools:
- VLAN Backed
- vCloud Network Isolation Backed (VCNI)
- Portgroup Backed
Each of these pools have specific requirements, recommendations and constraints and they will be listed below. However all of the three different types of pools are interchangeable; with that meaning a segment from a VLAN-Backed Pool and a Portgroup-Backed pool each offer the same functionality to your Org and vApp network and basically should be seen as a means of intra-Cloud transportation. Or to simplify it even further, it provides a wire. This wire enables VMs in a vApp to communicate to each other or vApps in an Org to communicate to each other. This also means, and that might sound very logical to some, the distributed vSwitch / Nexus / vSwitch needs physical uplinks in order to enable communication across multiple hosts in a cluster!
When is a segment of the network pool used? The answer is simple, whenever you create a vApp or Org Network which is not directly connected to the above layer a segment of your designated network pool will be used. Before you ask, the reason the network pool is not used in the case of a “directly” connected Org or vApp network is because the Org/vApp network is just a logical object in that case and the VM/vApp ends up directly in the portgroup the layer above. I will show you what that looks like in Part 3 of this series which will tie part 1 and 2 together including vShield Edge.
Now lets assume you created a VLAN-backed or a vCloud Network Isolation-backed pool. When an isolated or NAT routed vApp/Org network is created vCD will automatically instantiate a new network segment. This segment is essentially a portgroup on a distributed vSwitch. This portgroup will provide layer two isolation between the different segments. As a distributed vSwitch is used every host in your cluster will instantly have the same portgroups available. There is a very specific reason I only mentioned the VLAN Backed and the VCNI Backed pool, for the Portgroup Backed pool you will need to manually pre-create all portgroups and of course ensure all those portgroups are available on every host in the cluster.
To visualize it a bit more I took three screenshots. The first one shows the network pool. The pool is VLAN backed and holds VLAN 1000 through 1100 and these networks will be created on the distributed vSwitched labeled as “dvSwitch”:

Now that we have created a network pool we can create an isolated Org Network, in this case we create a fully isolated Org Network. This isolated org Network aka “Internal network” enables the vApps within your virtual datacenter to communicate to each other:
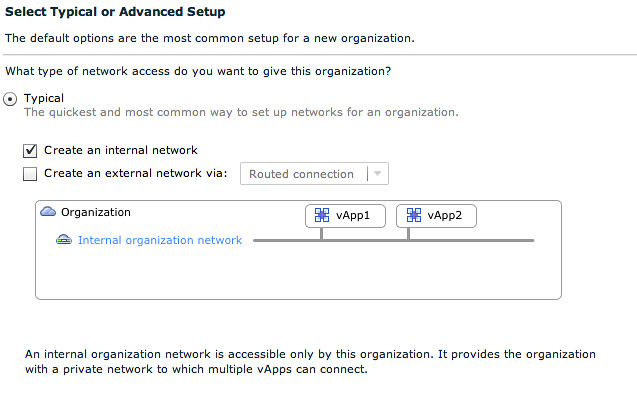
In order to be able to communicate we need a network segment. This network segment is provisioned from the Network Pool we created earlier, which was VLAN Backed.

After you fill out some of the other details and click “finish” a portgroup is automatically created within vSphere. Although difficult to read the portgroup name contains the Org Network and the VLAN ID. (VLAN 1008 and Org Network “YB-ISO-ORG”). You can even see the task at the bottom of the screenshot:

Hopefully that visualizes the process a bit more. I dropped some steps for the creation of the pool and the Org Network to keep it relatively simple. You can find a full detailed video here. Now as stated earlier each of the the three types of pools have very specific requirements and constraints I listed them below so you can make a decision based on the requirements or constraints you might have.
VLAN Backed
VLAN-backed network pools require availability of a set of unused VLANs. When an Org or vApp network is created which is based on a VLAN-backed network pool a portgroup is created on a dvSwitch and a VLAN is assigned to this portgroup. It should be noted that all VLANs specified for the pool will need to be trunked to the host and that in most environment the amount of available VLANs is limited.
- Requirements: Distributed vSwitch, pool of available VLANs, Physical uplinks need to support VLAN Trunks.
- Recommendations: n/a
- Constraints: Nexus 1000v and regular vSwitches are not supported currently, amount of available VLANs in most environments.
vCloud Network Isolation Backed
vCloud Network Isolation-backed(VCNI) network pools are flexible, easy to configure and do not require VLANs. vCNI provides layer 2 isolation by utilizing a network overlay. This network overlay is provided by MAC in MAC encapsulation and requires a vDS. For each consumed network vCloud Director creates a portgroup and assigns this portgroup a network ID number. This network ID number is used for the encapsulation of the traffic. As explained vCD uses MAC in MAC for the encapsulation of traffic. However, because of that the use of VCNI requires an increase in the MTU of the underlying transport network(dvSwitch) to avoid frame fragmentation due to the minor overhead cause by the MAC in MAC encapsulation.
Now this is a very thin explanation, but I don’t want to go to deep into this as it would only complicate things.
- Requirements: Distributed vSwitch
- Recommendations: minimum of 1 VLAN, MTU Increase (24Bytes, 1500 –> 1524).
- Constraints: Nexus 1000v and regular vSwitches are not supported currently.
Portgroup Backed
Portgroup-backed pools require pre-created portgroups within the vSphere environment. Portgroup-backed pools are in my opinion the least flexible of all three options. However, Portgroup-backed pools do not require vDS and can be based on vSS, vDS or Cisco Nexus 1000v which can be a specific customer or even platform requirement.
- Requirements: All portgroups need to be pre-created and available on all hosts of your cluster
- Recommendations: Use a scripted solution or host profiles to create the portgroups to ensure consistency
- Constraints: n/a
Wrapping up
Hopefully this clarifies network pools a bit. As explained, when creating and Org of vApp network which is not directly connected to the layer above a network of your Network Pool will be used to provide intra-cloud communication. For those who haven’t used vCD at all, believe me it took me a while to grasp these concepts so don’t be shy and ask questions/comment if anything is unclear.
Great information and excellent presentation, as usual, sir. 🙂
Nice article Duncan. Regarding vCD support with N1KV, please check out the VMware vCloud Director and Nexus 1000V Solution Brief: http://tinyurl.com/22jzudq. This contains some good information on using vCD with N1KV.
Great info…it most definitely help me understand things a bit better! I most definitely look forward to hearing more from you about vCD.
guys, you need part 4 to explain what’s going on when multiple ESX servers used , not just one ESX when all stuff is inside it which is not ‘real’ : you need to explain things like multiple VSE devices (one per port-group created for the same ORG) , NAT rules needed to pass packets through VSE between different networks , ‘internal pools’ actually acting like ‘external-direct’ when passing between ESX hosts (regular vlan on port-group in both cases) etc …it might be even more simple then the first parts …
http://www.yellow-bricks.com/2010/09/15/vcd-networking-part-3-use-case/
Great Info Dunchan. I also read on Kendrick’s block that VCNI network pool and External network have to be on 2 different VLANs. I understand external network has to be on a different vDS with a real VLAn tag. For VCNI pool, can i jsut make a VLAN ID and tag it on the port group i will be using for VCNI or does it have to be a real VLAN configured on the switch??
I think only a real VLAN will work, as the switch would otherwise drop the traffic
Hi Duncan!
is there any way to change VLAN id of existing Network Pool? This field is greyed in Properties. But we faced with situation when we need to use another vlan id.
Thanks ahead
I don’t know to be honest, never tried/tested that. I suggest contacting VMware support about this.
Thanks Duncan,
what about MTU for VCDNI, should it be increased in NetPool and physical equipment only, or also in dvswitch?
many thanks
Great post Duncan
I have a question, when i have a VLAN.backed network pool and an Org Network is created, how to avoid the automatic selection of VLAN ID and instead be able to manually assign a VLAN ID to an Org Network?
This is important for us to me able to migrate and deploy customers that have MPLS networks with VLAN already provisioned
Thanks a lot
Hi Duncan,
Great post! Can you please explain the creation of portgroup based networks as well. I have a single vlan configured on a portgroup on standard switch and already created a network pool from it. Now how can i create an external network?
Thanks,
-Manoj