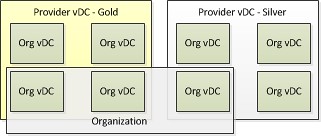
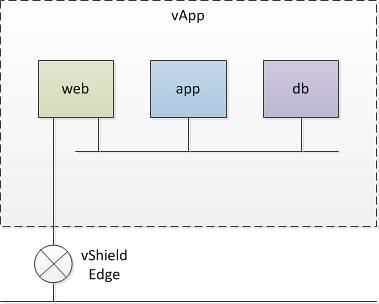
Internally I have seen this one a couple of times so I knew what the issue was, but outside of VMware not many people have played with VMware vCloud Director (vCD) yet. Here’s the full error that is shown when you create a NAT Router Org network of vApp network:
Error creating Shield network appliance.
– vClould-Shield edge error: Creating/configuring the VR failed: vsmHandle.initializeEdge() net:1948253845/dvportgroup-218 vse:vm-220 VSM IP:10.0.0.10 failed.
– HTTP/1.1 403 Forbidden – The user does not have permission to perform this operation.
This usually means that the vShield Edge license key has not been added to vCenter. You can simply add it as follows:
- From a vSphere Client host that is connected to a vCenter Server system, select Home > Licensing.
- For the report view, select Asset.
- Right‐click a vShield asset and select Change license key.
- Select Assign a new license key and click Enter Key.
- Enter the license key, enter an optional label for the key, and click OK.
- Click OK.
- Repeat these steps for each vShield component for which you have a license.
That should resolve this issue. Yes I agree, the error could have been more “user friendly” and I will ask the Engineering team if they can change this.