I did a couple of articles about vShield App a couple of months back. One of them explained how to get around a situation where vShield App would be down, as in this case of traffic would be blocked. Since then I spoke to multiple customers who asked me if it was possible to configure vShield App in such a way that traffic would be allowed when an issue occurred with vShield App. Although this goes against best practices and I would not recommend this, I can understand why some customers would want to do this. Luckily for them vShield App 5.0.1 now offers a setting that allows you to do this:
- Go to vShield within vCenter
- Click “Settings & Reports”
- Click the “vShield App” tab
- Click “Change” under “Failsafe”
- Click “Yes” when asked if you would like to change the setting
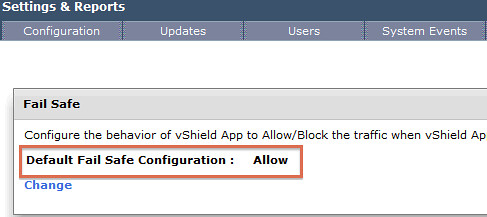
Together with the option to exclude VMs from being protected by vShield App and the automatic restart of vShield App appliances in the case of a failure it seems that my feature requests were fulfilled.
I think you want to allow all traffic to go through when vShield is down. I think many customers don’t want to have their production environment down because of a vShield bug or failure. On the other side, it’s a security risk..
I don’t agree and I think neither would many security officers. But the feature is there now, I just wanted to call it out and hope people will use it wisely and think before changing it.
I agree with Duncan I think the last thing you’d want is to allow all traffic when the firewall or vshield in this case is down. However our customers may have some use cases that require this behavior and now they at least have the option.
Many customers use vShield in addition to other security solutions. I think when vShield would go down once or twice due to bugs or something like that people (e.g. customers) would like to let the traffic go through when it’s down. It’s all specific to a customers solution. (I think :-))
Hi,
Is there a way to allow traffic for one group of VMs and block traffic for another group of VMs when vShield App is down.
Thanks,
nvizor
“this goes against best practices and I would not recommend this”
I would disagree with that; it’s _someone’s_ preferred practice for sure, especially for organizations with certain security requirements, but not generally accepted best practice. Your application owners don’t necessarily agree that an outage or stop of business is acceptable in case of a vShield failure.
In so much as a network outage is a security violation (loss of availability), just as bad an intrusion is a security violation, both can cost a serious amount of money. A 10 minute outage for an e-commerce site is a real large tangible cost; a 10 minute period during which there is a greater risk of intrusion is more of a theoretical cost.
Yes, by allowing traffic in case of failure there would be some loss of vShield protection during the outage. You can have an alert triggered for that minimize the outage; vShield should not be your environment’s only defense, and you can speak to the probability of an attack while vShield is down versus the certainty of a business impact that loss of availability will have.
I bet many security officers would not agree with that… anyway, I am just mentioning the best practice from a security stance. This should always be adapted to meet your own requirements and constraints.