I have seen this question popping up in multiple places now, vMotion over VXLAN is it supported? I googled it and nothing turned up, so I figured I would write a short statement:
In vSphere 5.1 (and earlier) vMotion over VXLAN is not supported.
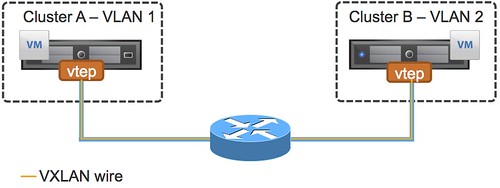
This statement might change in the future, it could be that in the next version vMotion traffic over a VXLAN wire will be supported, but with the current release it is not. Do note that vMotioning virtual machines which are attached to a VXLAN network is supported.
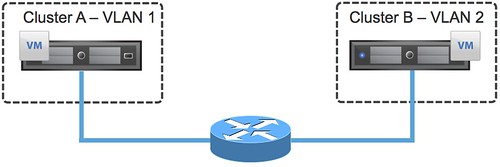
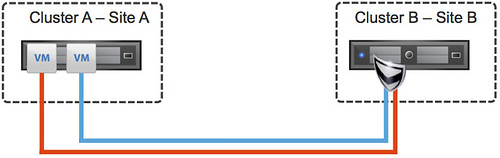
The next question people ask typically is, will it work? Yes it probably will, but again… it is not supported. Keep that in mind when you are designing a multi-site environment and want to use VXLAN.